Understanding the Risk

When it comes to addressing cybersecurity, the ramifications extend to the entirety of your organization — from the smallest processes to your organisation’s overall ability to function effectively. An attack that results in the leak of proprietary data can destroy your competitive edge. An attack that steals private customer data can result in lost public trust and lost revenue. An attack that paralyses even seemingly innocuous information systems can destroy your ability to operate and communicate effectively.
Cybersecurity involves more than understanding the capabilities and exposure of existing and emerging information technologies. It involves understanding that you are in an arms race with hackers. It involves understanding business needs, business processes, and the players involved in your business operations. It involves understanding where your greatest assets and your biggest risks are so you can focus and manage your investments to address relevant cyber threats. Improving cybersecurity is not a one-time solution. It’s a journey for business decision makers and IT leaders alike. And like any journey, it starts with a single step, followed by a few more steps.
Experiencing a cyber-attack is not a matter of if for your organisation. It’s a matter of when. And the time to prepare is now.
The following five steps can help you create an organisation that operates securely, that remains vigilant in the face of cyber threats, and that can show resiliency when attacked. The approach emphasises pragmatic solutions — solutions that are industry specific andthat deploy the right people, processes and tools to address known and emerging cyber threats. Businesses that take these five critical steps can transform themselves to become more secure, vigilant and resilient.
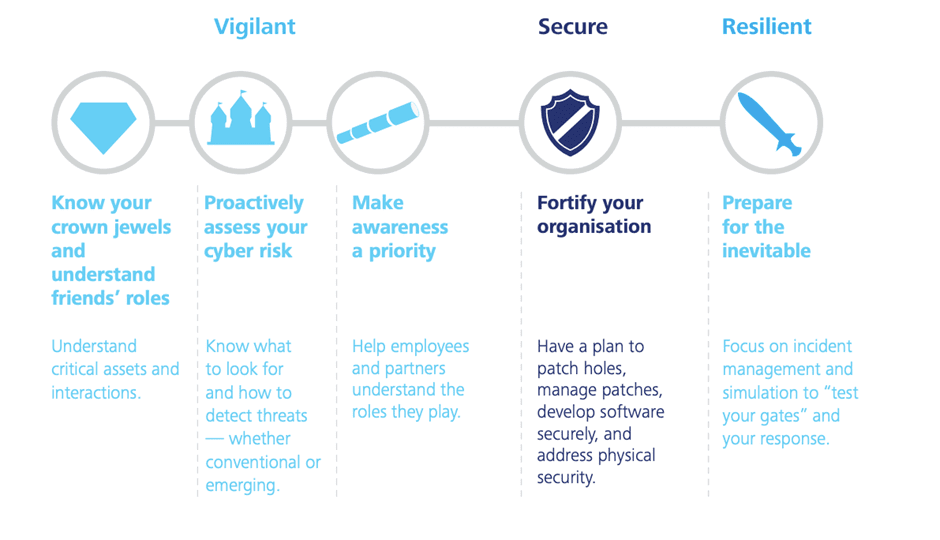
Step 1 – Know Your Crown Jewels
Cyber hackers continue to show an abundance of motivation. They need to be successful only once to see a payoff for their efforts. But your organisation must be successful in managing an attack each and every time. Your success depends largely on knowing the value of your information assets and knowing the risks to those assets. Know your “crown jewels” and understand your friends’ role in protecting them.
Remember:
- The level of sophistication in hacker goals and hacker tools continues to rise.
- Determining your crown jewels and the investments required to protect them will vary from industry to industry.
- Don’t prioritise your crown jewels based solely on business-continuity plans. Consider risk.
- Remember that your crown jewels can reside virtually anywhere — in the cloud, on mobile devices or with partners
Step 2 – Proactively Assess Your Cyber Risk
To address cyber threats effectively, organisations should have a cyber threat intelligence (CTI) capability that will help them rapidly identify, detect, and respond to threats.
Cyber threat intelligence involves using technology, processes, and people to proactively acquire, analyse, and disseminate intelligence internally and externally as a way to improve security. The CTI approach emphasises situational awareness and tactical/strategic responses that can help reduce the likelihood of harm or risk for your organisation.
Remember:
- Work towards a comprehensive plan for cyber threat intelligence.
- Be proactive. Seek new sources of information and new ways to interact with peers to identify trends and tactics.
- Monitor your data access trails and data logs to gain insight and detect threats early.
- Review log data to gain insight into potentially suspicious patterns or activities.
Step 3 – Make Awareness a Priority
Improving security relies heavily on awareness — an awareness of threats, risks, challenges and solutions within every department inside your organisation and within every partner organisation.
Security awareness should be more than a compliance exercise. Your aim should be to change your organisation’s security culture and the behaviour of employees. Building awareness is about building a culture.
Remember:
- Make sure employees and partners know that security measures are instrumental for your entire organisation.
- Explain security challenges and rules in language that users can understand.
- Think about awareness in a more interactive, on-going manner to engage workers and partners and to make threats seem more concrete.
Step 4 – Fortify Your Organization
Even though you know what your organisation’s critical assets are, that doesn’t make you secure. While the news is filled with accounts of cyberattacks that target unknown system weaknesses, most attacks exploit well known system weaknesses. The issue is straightforward: known vulnerabilities — vulnerabilities that are known to hackers and known to the organisations they target. The ultimate solution also can be straightforward: a targeted patch-management programme that focuses on crown jewels and critical assets.
Remember:
- Patch holes, focusing on critical holes as well as holes that might not seem critical but that are known.
- Resist the urge to lean too heavily on regular patches from a single major software provider.
- Work to spot physical security holes and weaknesses in data-access procedures
Step 5 – Prepare for the Inevitable
Most organisations have a security incident management process in place. But few have tested it. When, not if your organisation is attacked, how will you respond? How will the operational side of your organisation — and the communication arm of your organisation — react? How will the IT department react? How will they work together to understand the problem, remediate the problem, and let partners and customers know what’s going on? How will you contain the damage you may experience?
Remember:
- Know how departments will work together during a cyber-attack.
- Know how you will engage regulators as well as observers, such as privacy groups.
- Know how you will engage partners and customers.
- Simulate incident management, bringing in leadership, the board, operations and IT to test your preparedness.
Becoming a secure, vigilant, and resilient organisation doesn’t happen quickly. But it’s something that must happen if your organisation intends to survive, and even better, thrive amid the emerging technology landscape and the evolving terrain of cyber threats. Becoming a secure, vigilant and resilient organisation requires not only these five important steps; it requires constant assessment of how well you are carrying out those steps — constant assessment of whether you’re taking the steps effectively, and whether those steps are taking you where you want to go.
Despite the challenges, improving cybersecurity doesn’t have to be a gruelling journey. CSG Technologies can help. We know cybersecurity. We have deep experience addressing issues in a variety of industries, from manufacturing and logistics to architecture, design and healthcare. We’re up to date on the challenges that face organisations as they embrace cloud, mobile, social and analytics technologies. From strategy to implementation, we stand ready to assist you with the steps you need to take to get on your way.


