Table of contents

Cyber threat actors come in different forms and with various intentions. For instance Financial gain is an external cybercriminal’s motive, where as an insider threat may be motivated by discontent. As varied are the type of threat actors, so are types of businesses, government institutions, organizations and individuals who fall victim to their attacks. The recent election and the events surrounding COVID-19 have served to embolden threat actors, who are adopting evermore sophisticated and tactful tactics. For instance: In this year’s Microsoft digital defense report offered insight into threat actor’s relentless efforts to take advantage of remote working transition. Moreover, these are trends and observations gathered from thousands of security experts stationed across 77 countries world-wide. This study details the efforts made by threat actors to harvest data and information.
Taking Opportunity of Crisis
One such method that threat actors follow are capitalizing on the interest and fear related to disruptive situations, like the on-going COVID-19 pandemic. Threat actors pivot towards forging trusted sources in order to lure users to click on malicious links an attachments. The following graph depicts how actors have exploited people’s interests relative to the pandemic, especially at the initial stages of the outbreak in the US.
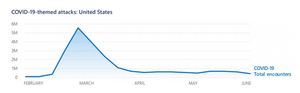
The sophistication associated with these cyber attackers is the way in which the attack is staged. Actors use the crisis situation to shield their presence within the victim’s computer operating system by compromising the network, exfiltrating data and by launching quick ransom attacks. Phishing And Business Email Compromise Another trend that has picked and escalated is the classic email phishing attack. Additionally, There are three main types of phishing expeditions that were unveiled. They are, credential phishing, Business Email Compromise (BEC) and combination of BEC and credential phishing.

1. Credential Phishing
Threat actors forge emails by posing as a trusted entities in order to lure victims to click corrupt attachments. After entering the operating system, actors maliciously gains access to sensitive information by means of compromised credentials. After gaining access to an operating system these attacks go on to launch data encryption programs and roots itself deeply within the organization’s data sources. This enables the threat actor to demand a ransom for the decryption key.
2. Business Email Compromise (BEC)
This is a type of phishing which targets mainly businesses. Unlike the classic phishing expeditions, BEC phishing impersonates a trusted associate such as the company CEO to release funds maliciously from other companies or within the company. These social engineered scams possess a level of sophistication that is capable of victimizing even savvy professionals. Threat actors reported to have invested chunks of resources and time to enhance this malicious technology.
3. Combination of BEC and Credential Phishing
This new form of kill chains combines the two forms of phishing expeditions. The attack starts off as credential phishing. Subsequently the actor gains access maliciously through a compromised credential and alters the ‘forwarding’ rule of the mailbox in order to monitor for financial transactions. These forwarding rules are engineered to harness mails with key words such as ‘invoice’, ‘accounts receivable’, ‘funds’, ‘overdue’ etc. into an email account fully controlled by the cybercriminal. The threat actor then steals the identity of the victim and misdirects employees to transfer wired transactions into actor’s pockets. The Microsoft Company reported to have blocked over 13 billion malicious mails, out of which 1 billion were URL based phishing threats in 2019. Furthermore they reported that they predict the rates would spike to 2 million such URL’s will be deployed per month for credential harvesting.
4. Ransomware Attacks
Microsoft recently launched an incident response engagement to curb ransomware attacks. Ransomware attacks have become more targeted and planned. For instance, threat actors launch their attacks on public holidays, when a company’s ability to respond is at it’s weakest. As a result, companies often give in to ransom demand to avoid facing greater losses incurred by down time. Sharing his views on ways to curb these pressing cyber security issues, the Microsoft Corporate Vice-President of Customer Security and Trust said that new rules and precautionary methods need to be enacted within the realms of cyber space. That businesses and organizations ought to invest in people and technology to help stop attacks. He also said that performing regular security updates, maintaining comprehensive backup policies and enabling Multi Factor Authentication (MFA) are essential proactive measures. Furthermore he emphasized that MFA stands out as the most effective method.
Here at CSG Technologies we provide IT security and business continuity plans which will fit your company’s requirements. Furthermore, we can assist with risk assessment, incident response and disaster recovery. Contact us today! And implement the best cyber security strategy for your business.
Do you want to read more on this topic? Check out these articles:
- The Six Main Types of Phishing Attacks and How to Protect Against Them.
- Cyber Deception Technology that Help Thwart Targeted Phishing Attacks
- Building A Human Firewall – Increasing Your Organization’s Cyber Resilience During the Pandemic
- Malware and Computer Viruses Facts and FAQs
- 15 Alarming Facts Every Modern Business Must Know


