
Table of contents
The line between safety and compliance is often blurred. Sometimes they sense like a shifting target, sometimes overlapping. Maybe you`ve requested yourself such a burning question:
- How can do we comply with security obligations?
- Is checking the compliance field honestly enough?
- How does all this allow the enterprise to characteristic and flow forward?
These questions determine the direction of the organization and ultimately lead to success or failure. In , this article will explain the difference between IT security and IT compliance.
So, what really is the difference between “Compliance” & “Security”?
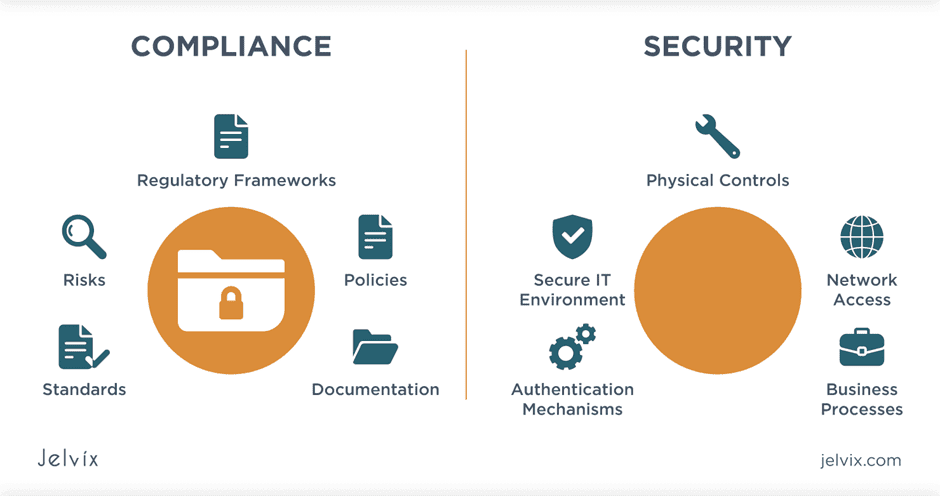
IT compliance is often misunderstood as synonymous with data protection and IT security. However, while the latter two deal with the concrete implementation of technologies and operational processes to protect digital systems and information, IT compliance deals with adherence to applicable requirements. Although the requirements – whether statutory, internal, or contractual – often result in specific requirements for IT security or data protection, IT security and data protection are often not limited solely to measures based on compliance. In addition, the regulatory requirements of lawmakers are often not phrased explicitly, but are instead based on principles. Companies are therefore not required to install solution XY to secure their IT.
Instead, every enterprise is purely chargeable for imposing the answers required to conform with the prescribed ideas consistent with its needs. Individual implementation is left to the organizations themselves.
Comparing IT Security & Compliance
Security is the implementation of effective technical management to protect corporate assets. Compliance is the application of that practice to meet third-party regulatory or contractual requirements.
Here is a rundown highlighting the variations among these concepts.
Security is:
- Practiced for its very own sake, now no longer to meet a 3rd party`s needs.
- Regular threats to an organization’s assets drive security as a shield of opposition.
- Never without a doubt completed and must be constantly maintained and improved
Compliance is:
- Practiced to fulfill outside necessities and facilitate commercial enterprise operations
- Driven with the aid of using commercial enterprise needs (hardly ever technical needs)
- Marked “Done” only when the third party is satisfied.
Primarily, a strict compliance-based approach to IT safety may fall brief of the mark. This mind-set specializes in simply doing the bare minimal required in an effort to fulfill necessities, which could result in extreme issues in an age of highly complicated malware and cyberattacks.
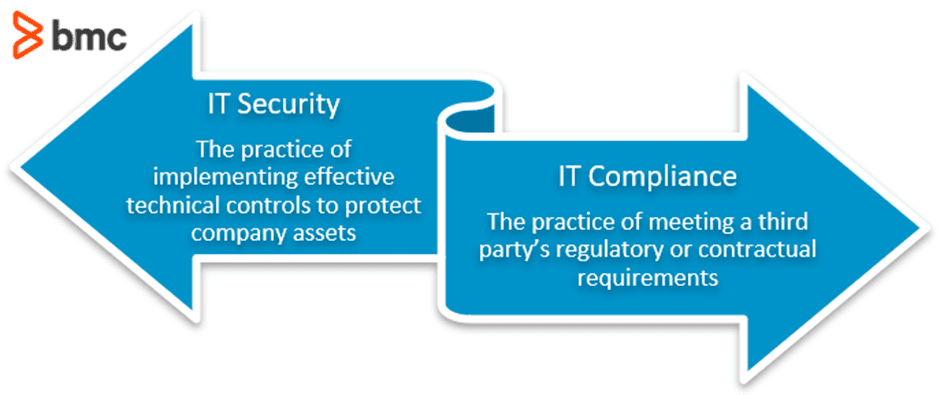
How does “Security” and “Compliance” work hand in hand?
We can all agree that organizations want a powerful IT Security application. Robust safety protocols and techniques permit your commercial enterprise to head past checking containers and begin using powerful practices to guard its vital assets.
This is wherein standards like defense-in-depth, layered safety systems, and consumer recognition education come in, in conjunction with everyday assessments with the aid of using outside events to make certain that those controls are honestly working. If a commercial enterprise had been centered totally on assembly compliance requirements that don`t require those vital functions, they could be leaving the door opened for attackers who prey on low-hanging fruit.
While compliance is referred to as doing the bare minimum, it`s beneficial in its very own right. Compliance is an asset to the commercial enterprise—it isn`t simply hoops you should leap through. Becoming compliant with a reputable enterprise fashionable like ISO:27001 can:
Bolster your organization`s reputation
Garner new commercial enterprise with safety-minded customers
Compliance also can assist you to become aware of any gaps present in your IT safety application. Most likely, it is possible these diagnoses may go unnoticed during a compliance audit. Additionally, compliance allows businesses to have a standardized safety application, in place of one wherein control can be selected on the whim of the administrator.
Security & Compliance are both business critical
The astute safety expert will see that safety and compliance move hand in hand while ensuring they complement every different region even though one might additionally fall short.
Compliance establishes a complete baseline for an organization`s safety posture.
Diligent safety practices construct on that baseline to make sure that the enterprise is protected from each angle.
With an identical consciousness on each of these concepts, an enterprise can be empowered to now effectively meet the requirements for its marketplace. Additionally, showcasing that it is going above and beyond in its dedication to virtual safety.

How do we gain “True Security”?
To summarize, ticking out the compliance boxes won`t cowl all of your safety wishes. It is highly likely to endanger treasured data and structures without protection. In order to be steady in addition to been compliant, you want a holistic, facts safety control system (ISMS) method that hyperlinks your controls right into a complete framework. Regulatory requirements can`t offer that framework alone, regardless of how prescriptive they are.
If you`re going through compliance challenges, it may be a cost effective and feasible option to discard those troubles as soon as they arise while leaving stressing about safety for later. However, Robust, cost-powerful and streamlined compliance is a right away effect of an powerful safety strategy—now no longer its foundation.
When information security is your key goal, each manage you implement, each well-known standard you`re licensed in opposition to and each audit you skipped demonstrably will increase your capacity to shield the pursuits of your clients, partners, personnel and owners/stockholders.
Shoot for safety and you`ll land in compliance each time. Shoot for compliance and you may land some distance, further from steady.


