
Overview
Hacking has always been a threat for internet users. However, COVID-19 has created opportunities for hackers to take advantage of people’s isolation and confusion. Therefore, it is important to be aware of signs of suspicious activity which ensures your online behavior is as safe as possible.
Here are few ways of figuring out whether you are hacked:
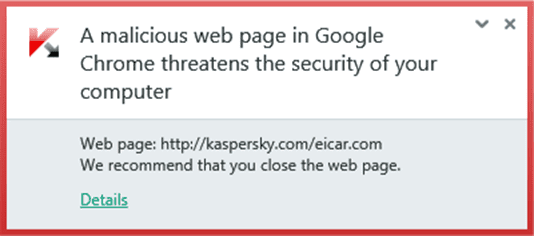
1) Receiving antivirus messages
a) Your computer system has the possibility of already been compromised.
b) Your computer system is fortunately not compromised beyond the pop-up message.
Sometimes, you cannot escape these fake messages without restarting your browser because usually these types of fake antivirus messages are configured to lock up your browser.
2) Unwanted browser toolbars
Unless, you recognize the source of the toolbar i.e., it is from a well-known vendor. If not, multiple new toolbars with names indicating that they are supposed to help you will appear on your browser.
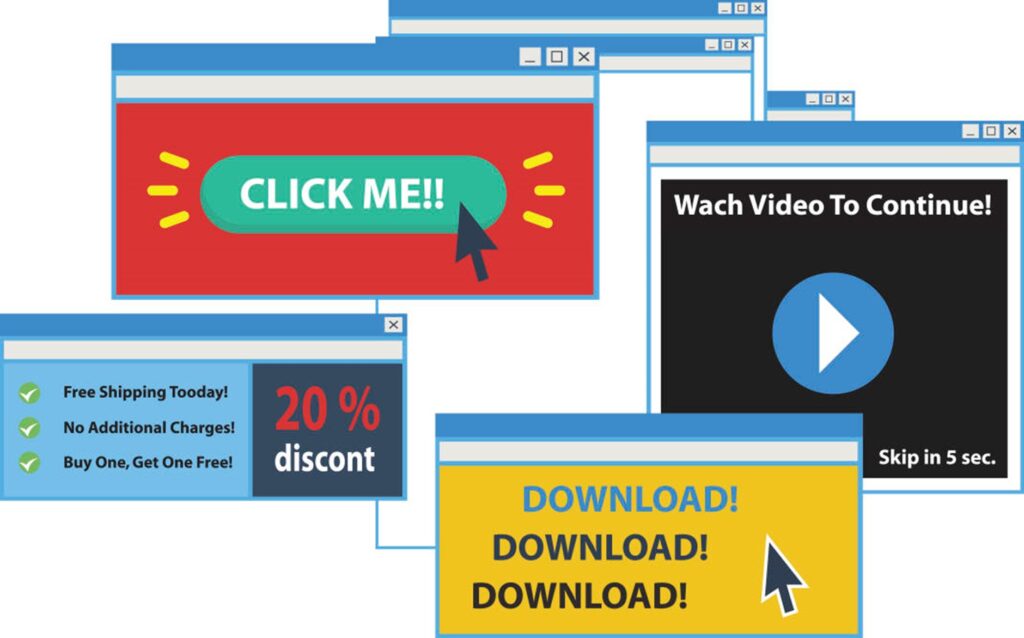
3) Random pop-ups become more frequent
Your system is likely to be compromised, if you are receiving random browser pop-ups from websites which usually don’t generate them.
4) Work colleagues,friends & family receive social media requests which were not sent by you.
a) Receiving an invitation again from a friend who you already remember connecting with on a specific social media.
b) A friend of yours receives a request from you again even though you both have been connected before.
Either way, there are ways to spot whether your account is compromised. Firstly, you notice that your friend’s social media lacks older posts and it is devoid of other recognizable friends or just a few. It is also possible that friends or anyone who has received such requests gets in contact with you to find out why you have been sending out new requests. he hacker could possibly be controlling your main social media site, or he/she could have created a second near-look-alike page.
5) Your online password isn’t working
A common sign of been hacked is when the password that you are 100% sure about stops working or it says incorrect password. However, before jumping to conclusions it is important to make sure it is not a technical problem with the website or system. Once certain, you can determine that your current password has been changed by a hacker. The threat actor has most likely logged in using your current password and changed it to keep you locked out.
In this scenario, the victim must have responded to an authentic-looking phishing email. The hacker purportedly claimed to be from a known service to the user, such as Amazon, in order to collect logon credentials. They change passwords to complicate recovery as they go on to use the victim’s identity for services and stealing money.

7) Important systems such as Antimalware, Task Manager or Registry Editor are disabled
Above all, this sign implies that there has been a major malicious compromise. You are most likely to have been exploited if your antivirus software is been disabled without your permission.

8)You’ve been notified by someone you’ve been hacked
An unrelated company’s notification is sometimes the only sign some companies receive news that they have been successfully compromised. Data Breach Investigations Report by Verizon revealed that unrelated third party companies notified companies that they were been hacked compared to organizations coming in to the realization that they were compromised. For instance, Microsoft revealed that in July 2018 nation-state attacks against were detected over 10,000 of its customers since the beginning of the year.
9) Strange network traffic patterns can be observed by the user
There have been countless instances where hacks were noticed due to unexpected network traffic patterns. The attack can take the form of transfers of large files to sites in countries where you don’t do business or it could also be due to distributed denial of service (DDoS) attack against your company’s web servers. Most importantly, if more companies were able to identify whether their network patterns are legitimate, there would be fewer cases of compromises. Likewise, there will also be a lesser need for a third party to confront them about how their network is compromised.
Conclusion
Malicious hacking originates from three common vectors: running Trojan horse programs, unpatched software, and responding to fake phishing emails. Thus, everyone should develop policies and implement technologies to thwart these vectos. However, it is nearly impossible to develop an antimalware program that is able to flawlessly detect malware and malicious actors.
Therefore, educating your employees and yourself to be cautious of common signs and symptoms of systems getting hacked is the key to battling cybercrimes. It is always important to start from scratch after an event where your system was compromised. Thereby, a complete computer restore after a data breach minimizes the risks of you getting caught in the trap again.
As always, if you need any help along the way, please feel free to reach out to our team at CSG Technologies and we will take care of you.



